How to Perform and Detect a Fake Update on Your PC
With this, you can understand common scams or pranks and how they work to recognize when something is off.

For many users who aren’t tech-savvy, encountering unfamiliar pop-ups on PC's can be overwhelming. Often, they rely on more experienced individuals to handle such issues.
Unfortunately, not everyone who offers to help is trustworthy. In some cases, these individuals can use fake update screens as a way to access your files or install malware, which can result in serious data or information breaches.
In this guide, we’ll walk you through how fake updates are set up and how to detect them on your system.
3 Steps to Perform a Fake Update
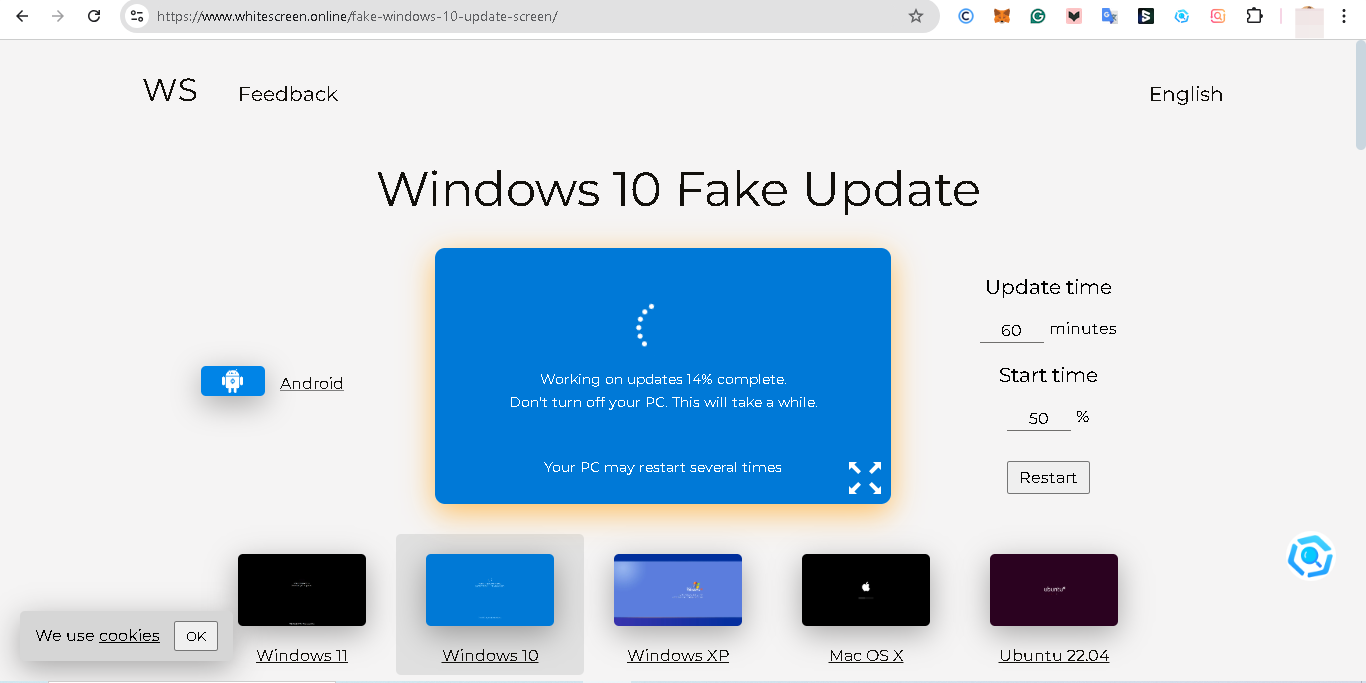
Step 1. Visit the WhiteScreen.online Site
Head over to your browser and visit the whitescreen.online website, which offers fake update screens mimicking various operating systems.
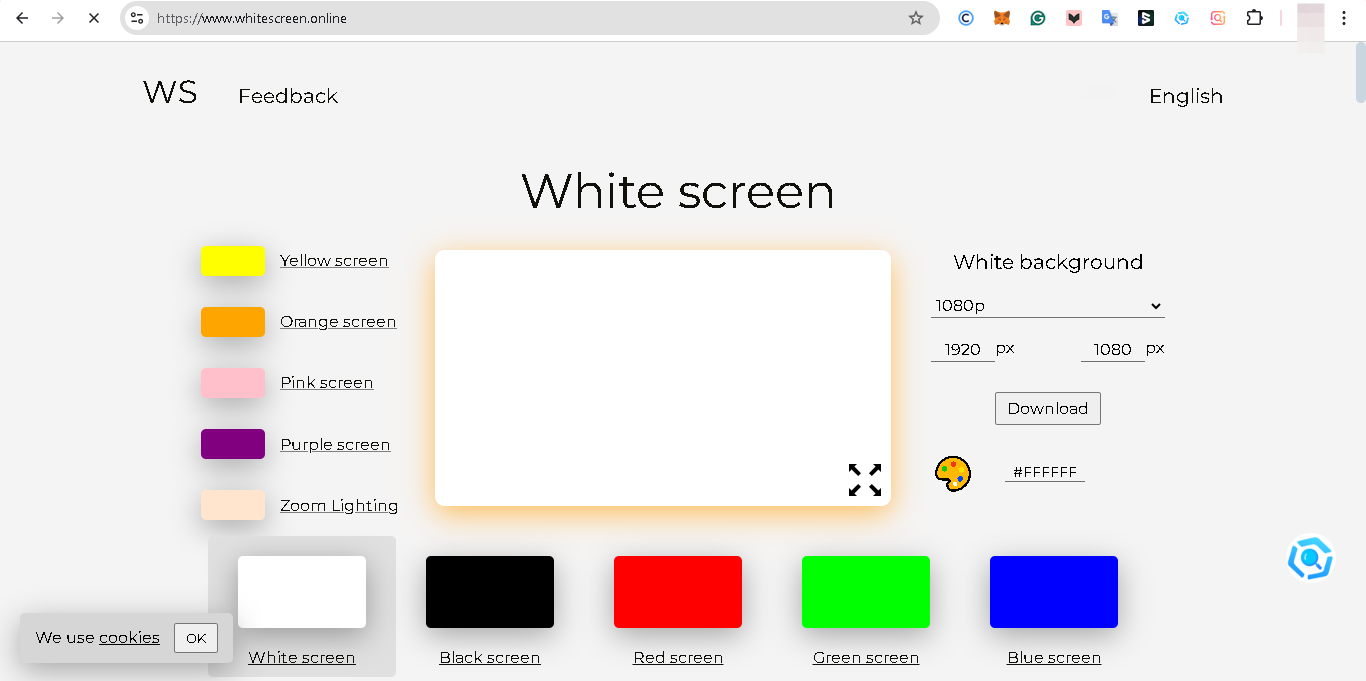
Step 2. Select Your Windows Version
Scroll down to the "Fake update screen" on the website and choose the version that matches your PC. For this guide, we’ll focus on Windows 10.
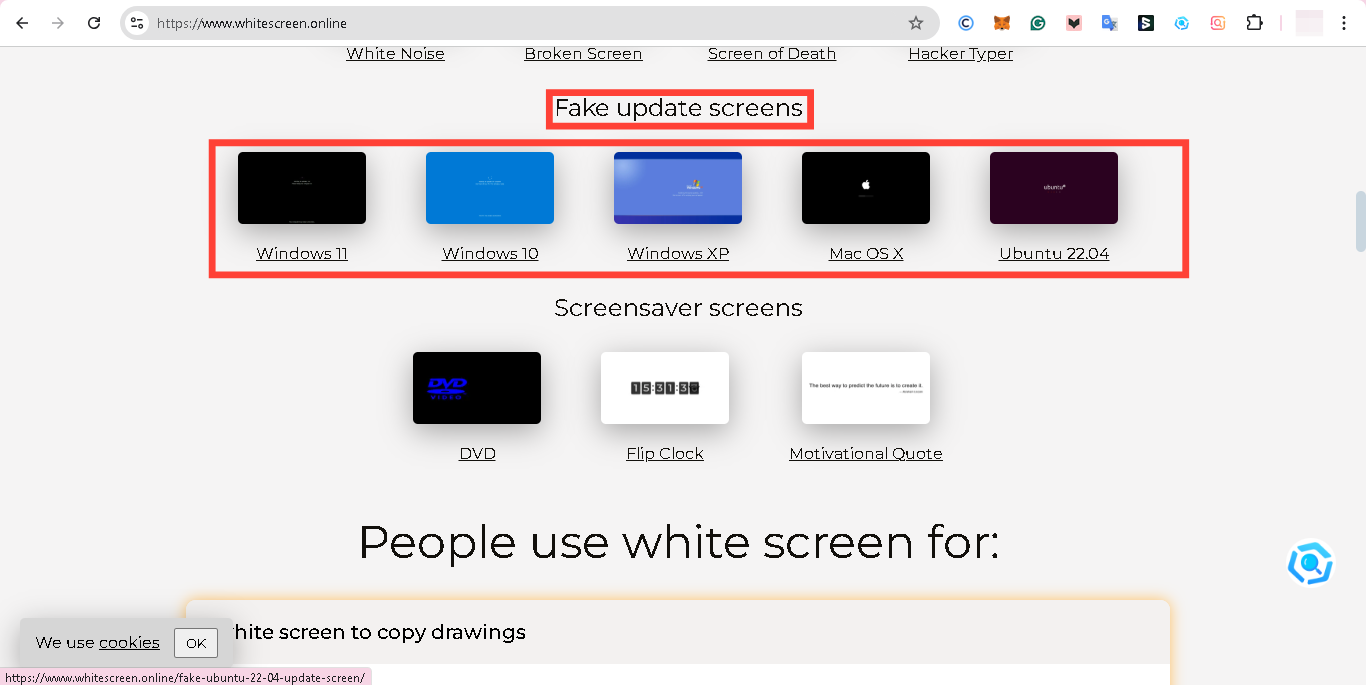
Step 3. Initiate the Fake Update Screen
Click on the "Windows 10" Update option. This will display a minimized-screen window that looks identical to a legitimate Windows update screen.
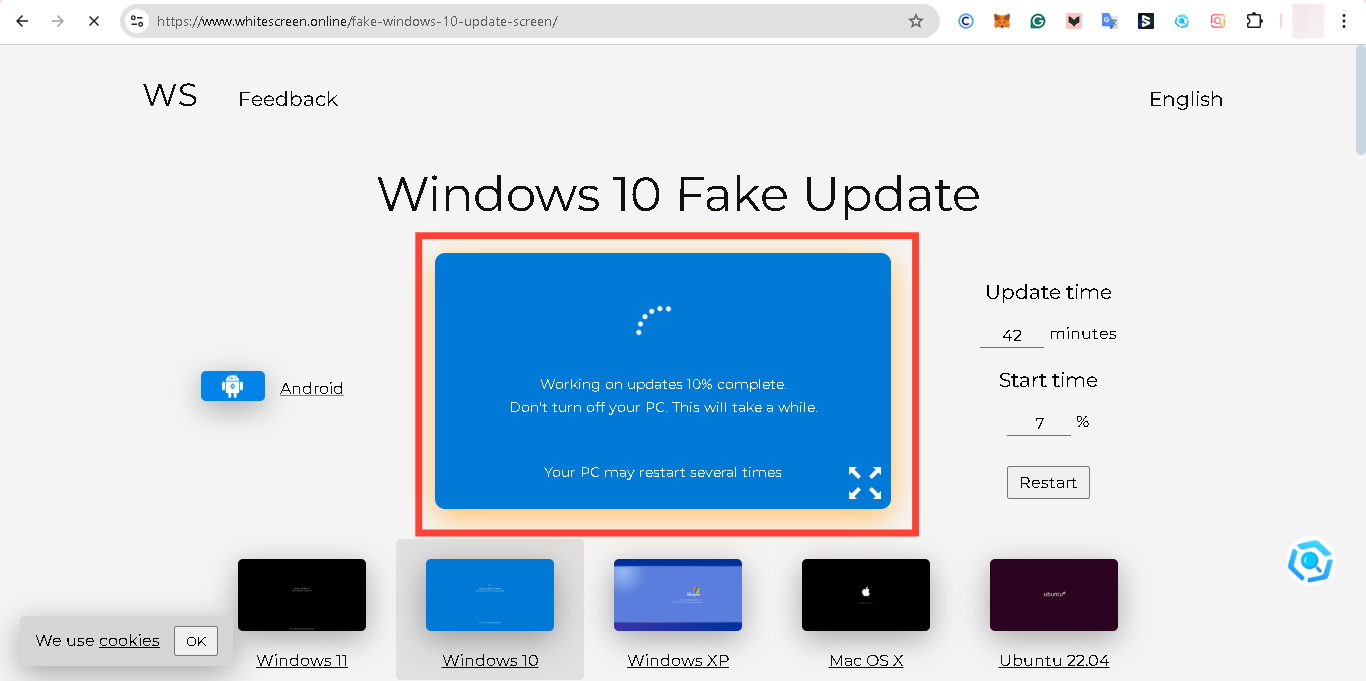
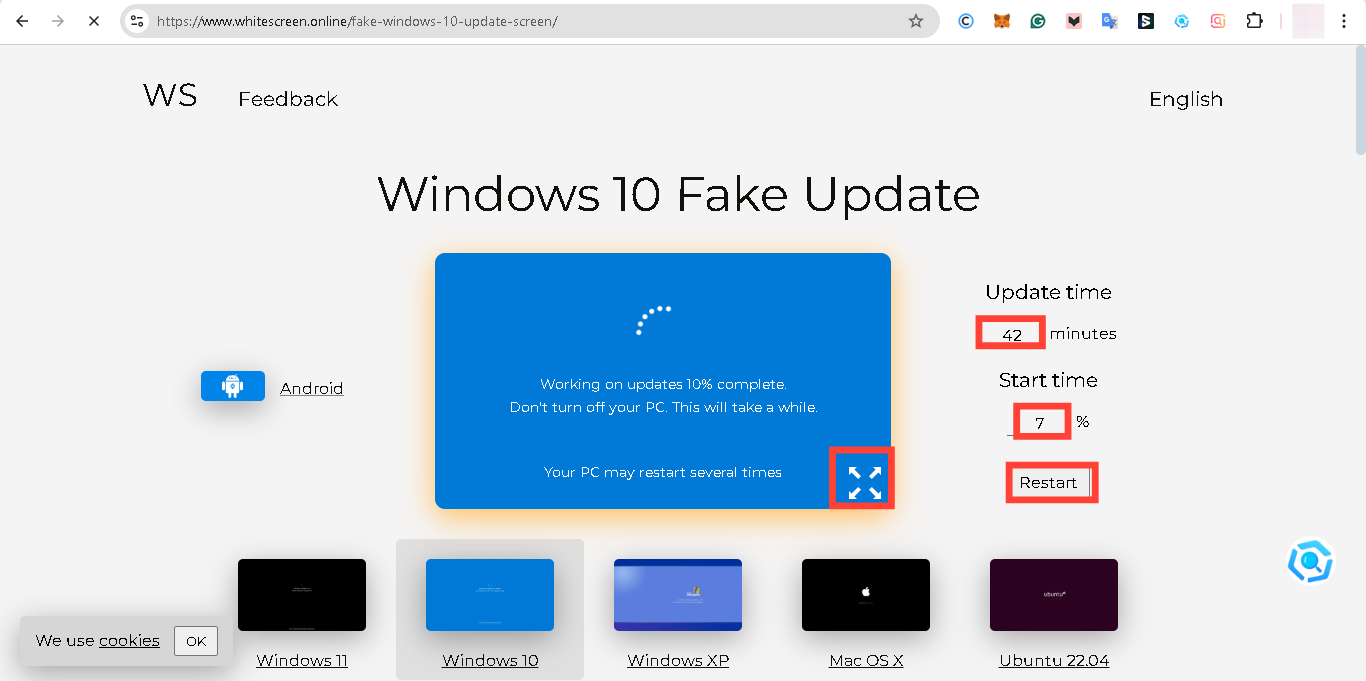
Step 4. Update Time and Start Time
Edit the "Update time" and "Start time" to prolong the fake update, then tap "Restart" to apply changes. After that tap the "Enlarge" icon. This will display a full-screen window that looks identical to a legitimate Windows update screen.
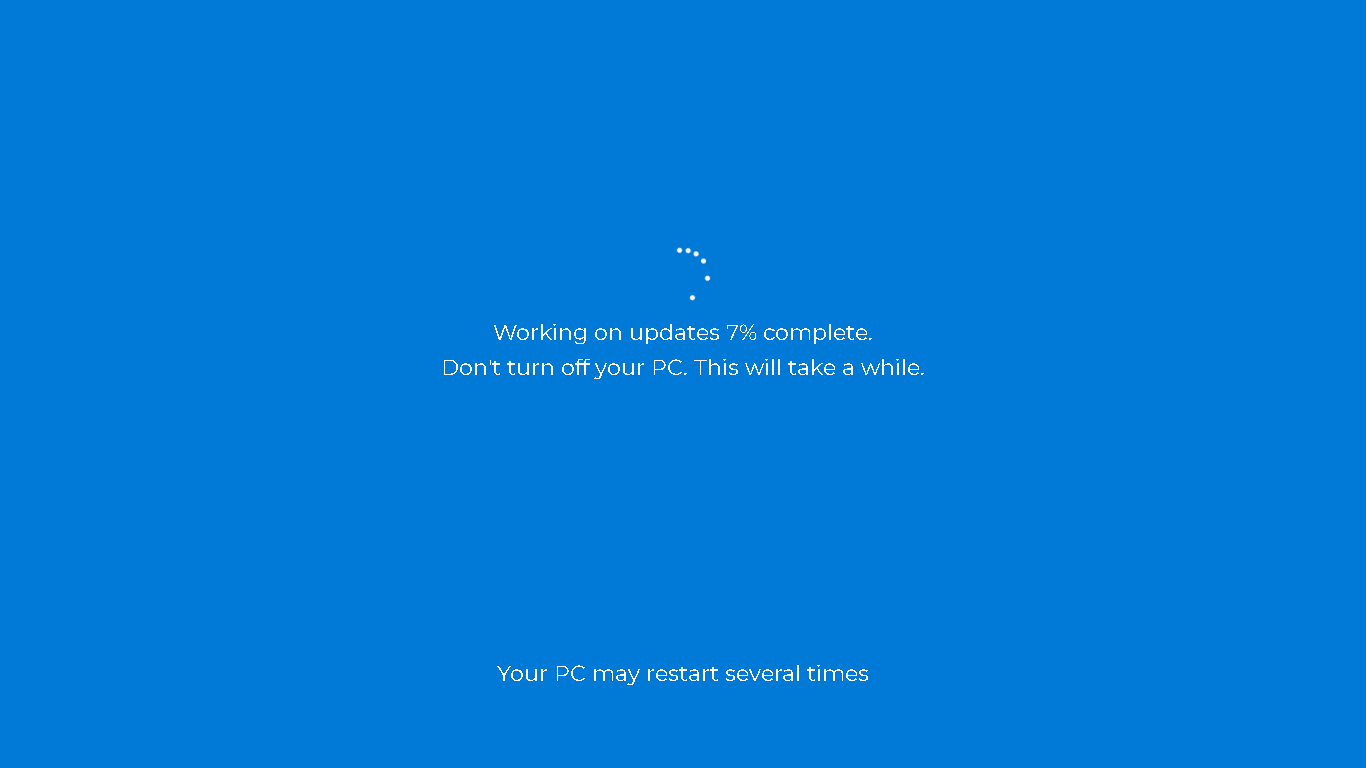
How to Detect a Fake Update
Step 1. Press the Escape (Esc) Key
If the update screen immediately disappears when you press the Esc key, it’s a fake. Real Windows updates won’t close this way.
Step 2. Check Task Manager
Another way to verify is by opening the Task Manager:
Press Ctrl + Shift + Esc to launch Task Manager.
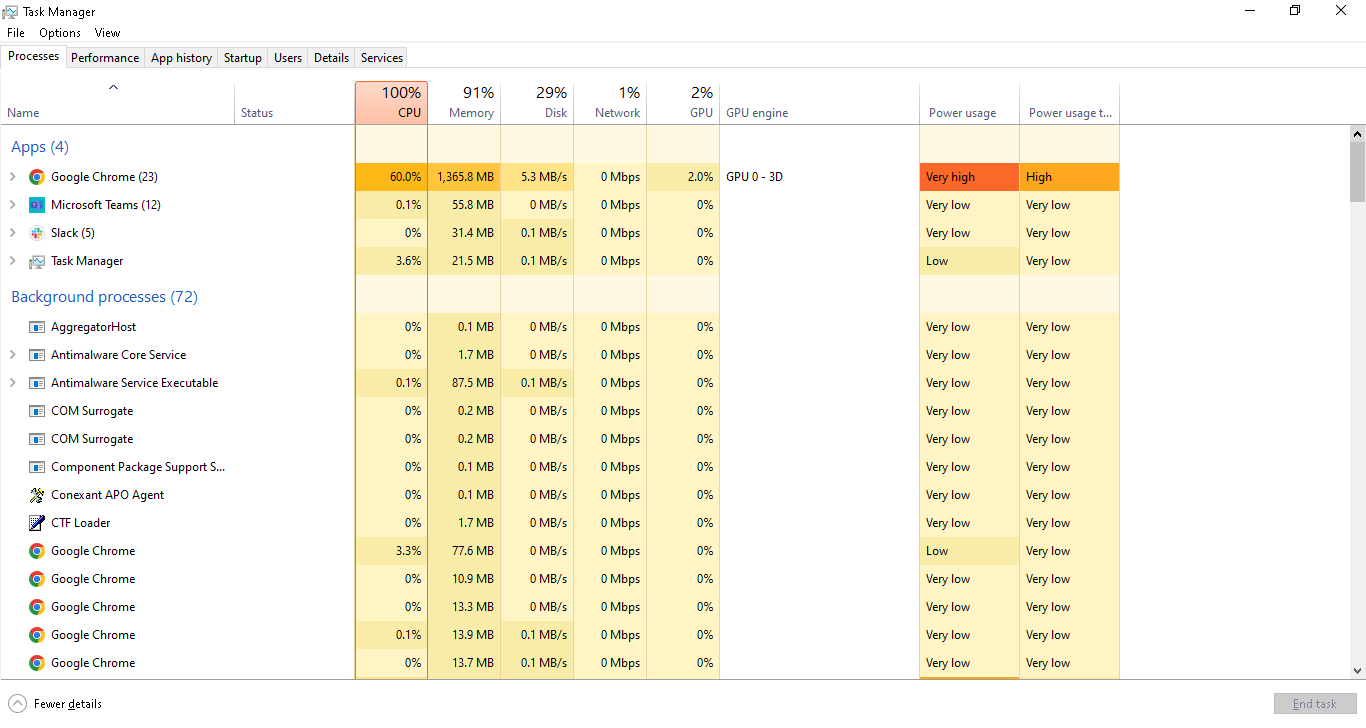
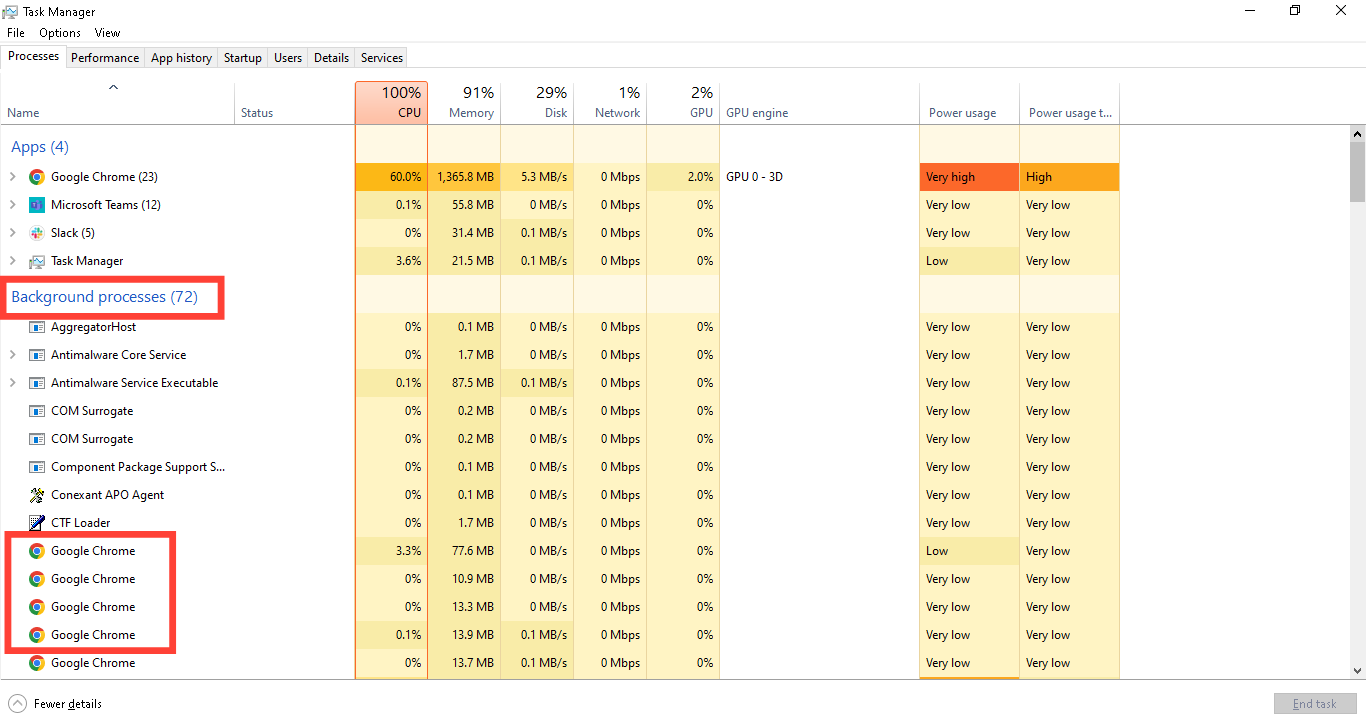
Look for unusual programs running. A real Windows update will be listed under "Windows processes", while a fake update might show as a browser window on "Background Processes".
Conclusion
Fake update screens can be used to deceive and steal data from unsuspecting users. That is why, knowing how to identify and close these screens is crucial for protecting your system. Follow this guide to stay vigilant and verify any updates before proceeding.
Image credit: David Adubiina/Techloy.com